How to Respond to a Data Breach
Read to learn how to strike the right balance between breach prevention and breach management.
Read to learn how to strike the right balance between breach prevention and breach management.
The following information is a part of our free cybersecurity and compliance Academy course.
No organization wants to find themselves in the middle of a data breach, but how you prepare for that possibility can determine how much damage it ultimately causes. Well-prepared businesses can diminish bad press, reduce negative impacts, and lower potential fines.
In this section, we’ll help you understand why you need to think about data breaches before they happen and why you need to have a tested incident response plan in place.
We’ll discuss how you can prepare for a data breach, what needs to be included in your incident response plan, and what to do if you are breached.
A successful data security program is all about striking the right balance between breach prevention and breach management. Both are crucial; both need your attention.
Use the tips from this section to better plan for a data breach at your organization.
Unfortunately, nearly every organization will experience system attacks, with some of these attacks successfully breaching an organization’s security.
If breached, and data is compromised, you may be liable and face serious fines. Depending on possible legal fees and fines, federal and municipal fines, and increased processing fees, you may have to pay for the following:
TOTAL POSSIBLE COST: $35,000 – $123,000+
TOTAL ADDITIONAL COST: $30,000 – $650,000+
TOTAL ADDITIONAL COST: $172,000 – $1.7 million+
TOTAL ADDITIONAL COST: Up to €20 million or 4% of your Global Annual Turnover, whichever is greater
A well-executed incident response plan can minimize breach impact, reduce fines, decrease negative press, and help you get back to business more quickly. In an ideal world and if you’re following security practices, you should already have an incident response plan prepared and employees trained to quickly deal with a data breach situation.
But if you don’t have a plan, employees will scramble to figure out what they’re supposed to do, and that’s when mistakes can occur. For example, if employees wipe a system without first creating images of the compromised systems, then you would be prevented from learning what happened, how much data was at risk, and what you can do to avoid reinfection.
No one wants to go through a data breach, but it’s essential to be prepared for one.
Different compliance mandates may require different breach procedures, especially regarding how, when, and who needs to be notified about a data breach. For example:
For PCI-related breaches, you need to alert all necessary parties immediately after discovering any suspected or confirmed unauthorized access, including payment card brands, merchant banks, and any other entities that might require notification by contract or law.
You’ll then likely need to provide payment card brands your PCI DSS compliance status with 48 hours (or less).
Within 72 hours, your organization must perform an initial forensic investigation and send your findings to payment card brands.
They will then likely require you to perform an independent forensic investigation, completed by a Payment Card Industry Forensic Investigator or PFI–who isn’t the same company you use for other PCI services. Then the PFI will make recommendations on how you should prioritize containment and secure cardholder data.
For HIPAA-related breaches, the Breach Notification Rule requires HIPAA covered entities and their business associates to provide notification following a breach of unsecured patient data.
Covered entities are just as liable if their business associate is found to be in breach of HIPAA requirements.
If you’re a covered entity, your statements must be sent to affected patients by first-class mail (or email if the affected individuals agreed to receive notices) as soon as reasonably possible. This must be no later than 60 days after breach discovery.
If 10 or more individuals’ information is out-of-date or insufficient or the breach affects more than 500 residents of a state or jurisdiction, post the statement on your website for at least 90 days and provide notice in major print or broadcast media in affected areas.
Covered entities also need to notify the Secretary of the HHS about the breach. If a breach affects fewer than 500 individuals, the covered entity may notify the Secretary of such breaches on an annual basis. But if a breach affects 500 or more individuals, covered entities must notify the Secretary of the HHS within 60 days following a breach (if not immediately).
If you’re a business associate, notify affected covered entities after discovering a data breach immediately (and no later than 60 days after discovering the data breach). Identify each individual affected by the breach and send this information to all affected covered entities.
For GDPR-related breaches, a PII data breach is a security breach leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data transmitted, stored, or otherwise processed.
Supervisory authorities must be told within 72 hours of when the controller becomes aware of a data breach where feasible, unless the controller can demonstrate that the breach is unlikely to result in risk to the rights of the data subject. If applicable, controllers may give reasons for delaying notification. But if individuals face an adverse impact, contact individuals directly.
Failure to report a breach when required to do so could result in a fine, in addition to the fine for the breach itself.
An incident response plan should be set up to address a suspected data breach in a series of phases with specific needs to be addressed. The incident response phases are:
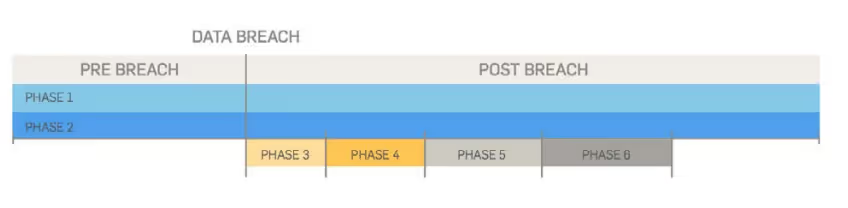
Preparation often takes the most effort in your incident response planning, but it’s by far the most crucial phase to protect your organization. This phase includes the following steps:
Identification (or detection) is the process where you determine whether you’ve actually been breached by looking for deviations from normal operations and activities.
An organization normally learns they’ve been breached in one of four ways:
It’s important to discover a data breach quickly, identify where it’s coming from, and pinpoint what it has affected.
When an organization becomes aware of a possible breach, it’s understandable to want to fix it immediately. However, without taking the proper steps and involving the right people, you can inadvertently destroy valuable forensic data. Forensic investigators use this data to determine how and when the breach occurred, how much data was accessed, and to help devise a plan to prevent similar future attacks.
When you discover a breach, remember:
Steps to consider during Containment and Documentation:
After containing the incident, you need to find and eliminate policies, procedures, or technology that led to the breach. This means all malware should be securely removed, systems should again be hardened and patched, and updates should be applied.
Whether you or a third party do this, you need to be thorough. If any trace of malware or security issues remain in your systems, you may still be losing sensitive data, increasing your liability.
Your incident response plan needs to be put in motion immediately after learning about a suspected data breach.
Recovering from a data breach is the process of restoring and returning affected systems and devices back into your business environment. During this time, it’s important to get your systems and business operations up and running again.
Remember, that before you consider reintroducing the previously compromised systems back into your production environment, you need to ensure that all systems have been hardened, patched, replaced, and tested.
After the forensic investigation, meet with all incident response team members and discuss what you’ve learned from the data breach, reviewing breach events in preparation for the next attack.
This phase is where you will analyze everything about the breach. Determine what worked well and what didn’t in your response plan. Then revise your incident response plan.
Creating an incident response plan can seem overwhelming. To simplify the process, develop your incident response plan in smaller, more manageable procedures.
While every organization will need varying policies, training, and documents, there are a few itemized response lists that most organizations need to include in their incident response plans, such as:
Proper communication is critical to successfully managing a data breach, which is why you need to document a thorough emergency contact/communications list. This list should contain information about: who to contact, how to reach these contacts, the appropriate timelines to reach out, and what they should say to external parties.
Your public response to the data breach will be judged heavily, so review your statements thoroughly.
Your system backup and recovery processes list will help you deal with the technical aspects of a data breach. This list helps you preserve any compromised data, quickly handle a data breach, and preserve your systems through backups. By creating and implementing this list, your organization can lessen further data loss and help you return to normal operations as quickly as possible.
A forensics analysis list is for organizations that use in-house forensic investigations resources. Your forensic team will need to know where to look for irregular behavior and have access to system security and event logs. If your organization doesn’t have access to an experienced computer forensic examiner in-house, you will want to consider vetting a forensics firm in advance with pre-completed agreements. This helps ensure you get an experienced investigator when you need it.
Your jump bag list is for grab-and-go responses (i.e., when you need to respond to a breach quickly). This list should include overall responses and actions employees need to take immediately after a breach. Your list will keep your plan organized and prevent mistakes caused by panic.
Your security policy review list deals with your response to a breach and its aftermath. This list helps you analyze the breach, so you can learn what to change. You should look at where your security controls failed, and how to improve them. The purpose of this list is to document the entire incident, what was done, what worked, what didn’t, and what was learned.
An incident response plan is only useful if it is properly established and followed by employees.
To help staff, regularly test their reactions through real-life simulations or what’s known as tabletop exercises. Tabletop exercises allow employees to learn about and practice their incident response roles when nothing is at stake, which can help you discover gaps in your incident response plan such as, communication issues.
In a discussion-based table exercise, you and your staff discuss response roles in hypothetical situations. A discussion-based tabletop exercise is a great starting point because it doesn’t require extensive preparation or resources, while still testing your team’s response to real-life scenarios without risk to your organization.
However, this exercise can’t fully test your incident response plan or your team’s response roles.
In a simulation exercise, your team tests their incident responses through a live walkthrough test that has been highly choreographed and planned. This exercise allows participants to experience how events actually happen, helping your team better understand their roles.
However, simulation exercises require a lot of time to plan and coordinate, while still not fully testing your team’s capabilities.
In parallel testing, your incident response team actually tests their incident response roles in a test environment. Parallel testing is the most realistic simulation possible and provides your team with the best feedback about their roles.
However, parallel testing is more expensive and requires more time planning than other exercises because you need to simulate an actual production environment.
Question 1:
Should your organization have an incident response plan set up to address a suspected data breach? (Choose only ONE best answer.)
Question 2:
How often should you review your incident response plan? (Choose only ONE best answer.)
Question 3:
A well-executed incident response plan can: (Choose only ONE best answer.)
Question 4:
TRUE OR FALSE: An incident response plan is only useful if it is properly established and followed by employees. (Choose only ONE best answer.)
Answer Code: Q1: 1, Q2: 3, Q3: 5, Q4: 2