Discover what the difference is between a penetration test and a vulnerability scan.
Developing and implementing an incident response plan will help your business handle a data breach quickly, efficiently, and with minimal damage done.
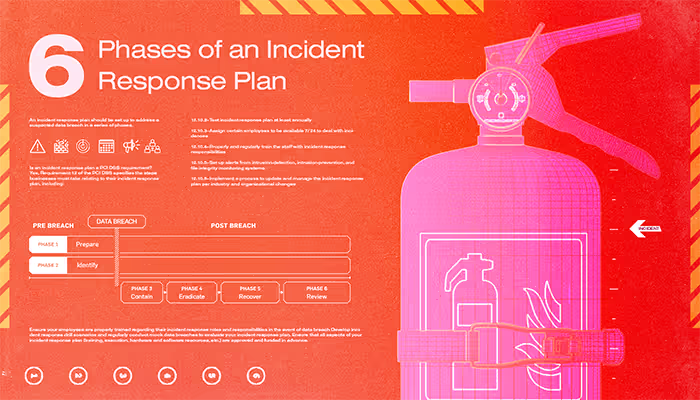
An incident response plan should be set up to address a suspected data breach in a series of phases.

GDPR is regulation that will help unite privacy laws across Europe. Here are some answered questions about GDPR Compliance.

Vulnerability scans search your network and provide a logged summary of alerts you can review and act on. Here are the top 15 ASV scan vulnerabilities and how to fix them.

a risk assessment can be the most important part of your overall security and compliance program, since it helps you identify systems, third parties, business processes, and people that are in scope for PCI compliance.

Healthcare organizations of all sizes use firewalls to protect the perimeter of their sensitive networks. Here are some firewall best practices to get you started.

Determining which type of pentests are best for your organization depends on concerns or needs that are generated from real life security incidents or concerns about security posture for business critical systems or environments.

Performing an SAQ D Service Provider version 4.0 Self-Assessment: Updates and changes in the new 4.0 standard.
The Apache Struts project has just released a security bulletin about a new critical vulnerability in the Apache Struts web application framework. Here's how to protect yourself.

The SAQ B is designed for merchant environments where all cardholder data is processed using standalone Point-of-Interaction (POI) terminals connected via an analog phone line.
While convenient, mobile devices on your network can pose a risk to your business.

Learn more about SAQ P2PE and who qualifies for it.

If you have a knack for solving problems, good organizational skills, and attention to detail, cybersecurity might be a good fit for you.

PCI PIN refers to the security requirements and assessment for merchants that accept, process or transmit payment card personal identification numbers (PIN).

Amid the chaos and uncertainty, SecurityMetrics remains steadfast in our mission to help you close compliance gaps and prevent data breaches. We stand ready to help with your security concerns, education, and content needs at this time.

Merchants who do not qualify to assess their PCI DSS compliance using any of the simpler self-assessment questionnaires are required to use the SAQ D to validate their compliance.

The way you handle emailing credit card info might just change your scope for PCI DSS compliance.
Your reception desk might be one of the most vulnerable locations in your entire organization for a data breach. W

See the step-by-step ways the average hacker looks for valuable data and what hacking victims should do in response to an attack.

All businesses that handle payment card data, no matter their size or processing methods, must follow these requirements and be PCI compliant.